Posted on Wednesday, March 14 2012 @ 12:14 CET by Thomas De Maesschalck
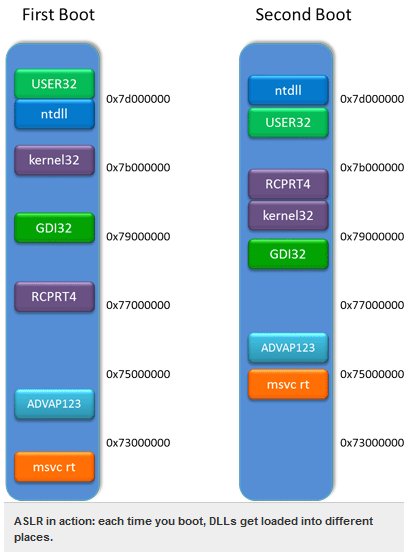
Microsoft disclosed some information about the new mitigation techniques that will be used in Internet Explorer 10. The Windows 8 operating system will feature an improved Address Space Layout Randomization (ASLR), a technique that makes it harder to take advantage of software flaws by randomizing the memory location of DLLs.
These techniques are all additive. Before these mitigation techniques, attackers could insert the code they wanted to execute directly into overflowed buffers and trick the program into executing it. With DEP, that became impossible: the buffer could be readable, but not executable.
Attackers came up with a couple of clever techniques around this, "return to libc" and "return-oriented programming." With both of these techniques, the attacker took advantage of the fact that the program's executable and its libraries (DLLs) were already executable. With return to libc, the attacker would use the buffer as a kind of input to one of these executable functions. Return-oriented programming generalizes this technique; here the attacker would use the buffer to jump between lots of small fragments of these executable DLLs.
ASLR in turn is created to combat these techniques; both of them depend on the DLLs being in predictable locations in memory; the attacker includes the addresses of the different pieces of executable code it wants as part of their attack. By shuffling DLLs around in memory, this predictability no longer exists.
Full details
at ARS Technica.