
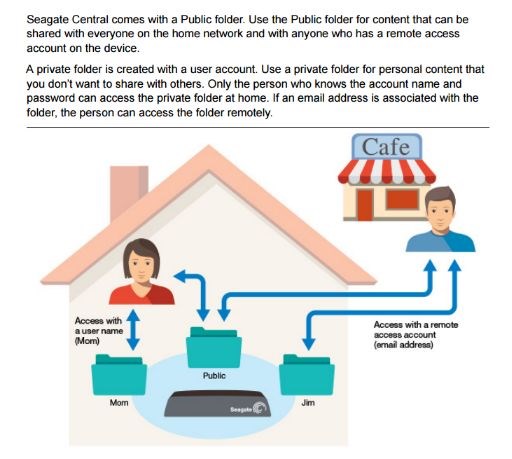
The Seagate Central NAS has a public folder that can't be deactivated or deleted, and is accessible to all users, even anonymous users. The Miner-C malware abuses this design flaw to spread itself to the public folder on all Seagate Central NAS devices it can find by scanning the Internet for potential victims.
The next step of the attack vector is to trick the user into installing the malware. This is done by placing "Photo.scr" in the public folder, this is a script that malware coders have modified to use a standard Windows folder icon.
By default, Windows hides most file extensions so when a Seagate Central NAS device owner explores the public folder chances are high their curiosity will be peaked by this fake Photo folder. When the user clicks on the script, the cryptocurrency miner is installed on their PC.
Sophos security researchers discovered that of the around 7,000 Seagate Central NAS devices connected to the Internet, about 5,000 are infected with Miner-C. Because the Monero account information is stored in the malware's configuration file, the researchers were able to calculate that these cybercriminals have made over $86,400 from the operations and are responsible for 2.5 percent of the entire Monero mining activity.
As Softpedia reports, one of the big worries here is that users have no way to protect their device without completely disabling remote access:
The quandary is that Seagate Central owners have no way to protect their device. Turning off the remote access NAS feature can prevent the infection, but also means they lose the ability to access the device from a remote location, one of the reasons they purchased the hard drive in the first place.