Posted on Friday, November 10 2017 @ 12:38 CET by Thomas De Maesschalck
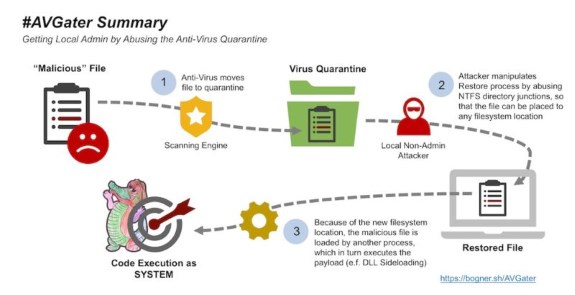
Security researcher Florian Bogner found a vulnerability in close to a dozen anti-virus tools that can be used to perform an attack that would otherwise be impossible. The AVGater exploit makes it possible to gain full control over a system, by getting the foot in the door by abusing bugs in anti-virus quarantine operations. The big catch here is that the hacker needs local access, so this is primarily for high-value targets and not for random home PCs.
AVGater, as the researcher is calling the vulnerability, works by relocating malware already put into an AV quarantine folder to a location of the attacker's choosing. Attackers can exploit it by first getting a vulnerable AV program to quarantine a piece of malicious code and then moving it into a sensitive directory such as C: Windows or C: Program Files, which normally would be off limits to the attacker. Six of the affected AV programs have patched the vulnerable after it was privately reported. The remaining brands have yet to fix it, said Florian Bogner, a Vienna, Austria-based security researcher who gets paid to hack businesses so he can help them identify weaknesses in their networks.
Full details
at ARS Technica.