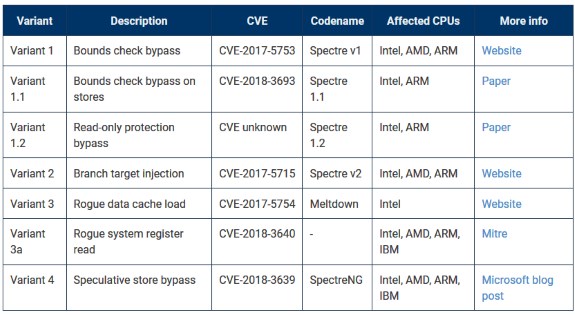
Next we have Spectre 1.2, a vulnerability that enables writing to CPU memory sectors that are usually protected by read-only flags. The new bug impacts both Intel and ARM, and probably AMD too. More about both vulnerabilities can be read at BleepingComputer.
"As a result [of malicious Spectre 1.2 writes], sandboxing that depends on hardware enforcement of read-only memory is rendered ineffective," researchers say.
To exploit, similarly to most previous Meltdown and Spectre bugs, both vulnerabilities require the presence of malicious code on a user's PC, code responsible for running the attack. This somewhat limits the bug's severity, but doesn't excuse sysadmins who fail to apply patches when they'll become available.