
Kaspersky Lab offers coverage over here. The worm is called WannaCry (or Wcry) and uses the "EternalBlue" SMB exploit from the NSA. This exploit was leaked to the Internet via the ShadowBrokers dump about a month ago.
The WannaCry worm uses a Windows vulnerability that enables it to spread automatically via internal LAN and WAN, without requiring any user action. That's why it's causing so much ruckus, once it's inside a vulnerable network it can rapidly replicate itself.
A few hours ago, Spain’s Computer Emergency Response Team CCN-CERT, posted an alert on their site about a massive ransomware attack affecting several Spanish organizations. The alert recommends the installation of updates in the Microsoft March 2017 Security Bulletin as a means of stopping the spread of the attack.All Windows operating systems from XP to 10 are vulnerable but the good news is that Microsoft patched this vulnerability on March 14, 2017 (MS17-010). So based on current knowledge, it appears organizations that got hit big by this worm are either using unsupported software like Windows XP or neglect to install security updates on a regular basis. Patched systems can get infected too but this will require a user action.
The National Health Service (NHS) in the U.K. also issued an alert and confirmed infections at 16 medical institutions. We have confirmed additional infections in several additional countries, including Russia, Ukraine, and India.
It’s important to understand that while unpatched Windows computers exposing their SMB services can be remotely attacked with the “EternalBlue” exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn’t really prevent the ransomware component from working. Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak.
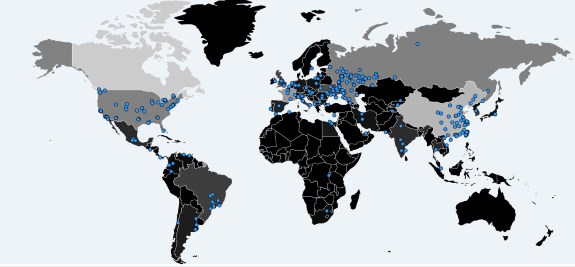
Here's an infection map from MalwareTech botnet tracker.
Here's what a London GP sees when trying to connect to the NHS network pic.twitter.com/lV8zXarAXS
— Rory Cellan-Jones (@ruskin147) 12 mei 2017