
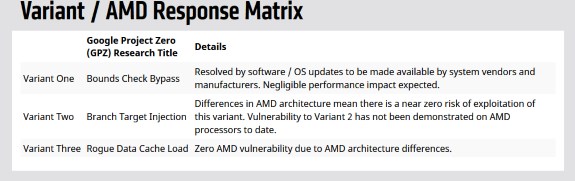
First up, AMD downplayed Intel's comment that AMD and ARM processors have similar vulnerabilities. While AMD acknowledged that it's processors are not immune, it said the risk is near zero at this time:
To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD's architecture, we believe there is a near zero risk to AMD processors at this time.
And now the big news, security researchers published a lot of information about what's going on. So far this was all kept under wraps but now we know that there's not one attack but two. The first one is known as Meltdown, this vulnerability is found in every Intel processor that's been on the market since the Pentium days!
This bug is the most serious one of the two, hackers can abuse the CPU bug to read the kernel memory and the entire physical memory of target PCs. The severity of this bug sparked panic in the security community and resulted in far-reaching emergency patches. Basically, this exposes all your secrets and it's especially dangerous in shared environments like cloud computing. The attacks are hard to detect and leave no traces. But for regular desktop users the risk is less significant because attackers can't exploit these vulnerabilities without first gaining access to the target PC via a different method.
Meltdown is a hardware bug that targets a specific speculative execution feature. It can not be fixed via a CPU microcode update. The only solution is to remove shared kernel mapping, which comes at a performance cost. The performance impact heavily depends on the use case, games are expected to see little impact but software that performs a lot of disk or network operations can see a huge performance drop.
Software updates for Meltdown are rolled out as soon as possible. Windows 10 received an out-of-band update yesterday, the Linux kernel received updates, macOS High Sierra 10.13.2 is not vulnerable and Google rolled out updates as part of the Android January security bulletin.
Intel hinted yesterday that AMD and ARM are also affected. It appears the company was talking about Spectre, which is a second vulnerability that enables attackers to read contents of memory from other user's active programs. Spectre affects processors from AMD, ARM and Intel. It exploits a wider range of speculative execution features and the bad news is that it can't be completely fixed without major changes to CPU architecture design.
Owners of AMD and ARM systems shouldn't rest easy, though, and that's thanks to Spectre. Spectre is a more general attack, based on a wider range of speculative execution features. The paper describes using speculation around, for example, array bounds checks and branches instructions to leak information, with proof-of-concept attacks being successful on AMD, ARM, and Intel systems. Spectre attacks can be used both to leak information from the kernel to user programs, but also from virtualization hypervisors to guest systems.A bit more in-depth information about how Meltdown and Spectre work can be found at ARS Technica.
On a related note, the news is raising suspicion about a big $24 million stock sale from Intel CEO Brian Krzanich. He sold millions of dollars worth of stock last year, after the chip giant was informed of the vulnerabilities. Interestingly, Krzanich brought down his stockholding to exactly the 250,000 share threshold that he must meet as Intel CEO. An Intel spokeswoman denies the share sale was related to Meltdown and Spectre.