The Regin malware, whose existence was first reported by the security firm Symantec on Sunday, is among the most sophisticated ever discovered by researchers. Symantec compared Regin to Stuxnet, a state-sponsored malware program developed by the U.S. and Israel to sabotage computers at an Iranian nuclear facility. Sources familiar with internal investigations at Belgacom and the European Union have confirmed to The Intercept that the Regin malware was found on their systems after they were compromised, linking the spy tool to the secret GCHQ and NSA operations.
Security researchers from Symantec announced the discovery of "Regin", a highly sophisticated piece of malware that stayed under the radar for at least six years. Symantec says everything points to Regin being a primary cyberespionage tool of a nation state, but who's doing the spying remains a mystery.
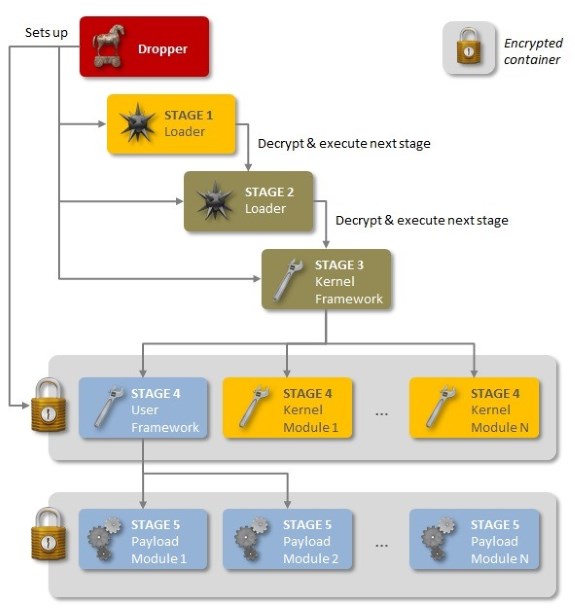
Regin uses a multi-stage attack system, each stage is encrypted and none by themselves are revealing about the overall attack. The trojan uses a custom-made encrypted virtual file system as well as other non-standard techniques as a means of stealth. Symantec believes many components of Regin remain undiscovered but discovered that there are two variants of Regin. Initial attacks were committed between 2008 and 2011, after which the malware disappeared until the arrival of an updated, 64-bit Regin 2.0 trojan in 2013.
Symantec has not found a stage 3 for the 2.0 version, which may be explained by the fact that the 1.0 stage 3 is a device driver, and installing device drivers on 64-bit Windows surreptitiously is a difficult proposition even, it would seem, for the most sophisticated of attackers.
Symantec's description in their threat database of the threat, where they call it Backdoor.Trojan.GR, indicates that it was detected and protection provided on December 12, 2013. Presumably they did not know what they had until much more recently, and retrospective analysis revealed the true nature of the threat and its use prior years.
Even so, there is still much about Regin that they do not understand. They have, for example, not identified a reproducible infection vector, and these may have been customized for attacks. There are also "dozens of Regin payloads," providing for all the usual things like password stealing, captured screens, stolen files — including deleted files — and more.
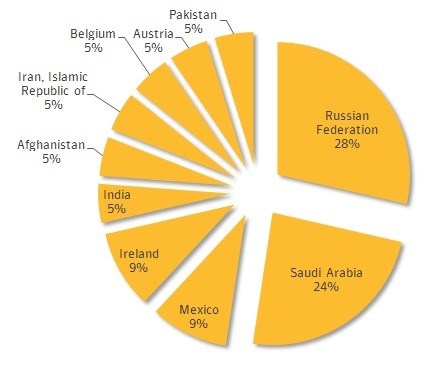
A look at a chart of Regin infections by country reveal just over half of all infections targeted Russia and Saudi Arabia. Ireland and Mexico both accounted for 9 percent of attacks, while the remaining 30 percent of attacks was split evenly between India, Afghanistan, Iran, Belgium, Austria and Pakistan.
Source: ZD Net