Earlier versions of the malware supported Maxtor, Seagate, WD, and Samsung but newer, upgraded modules added support for HGST, IBM, Hitachi, ExcelStor, Micron, Toshiba, OCZ, OWC, Corsair and Mushkin so pretty much all storage devices, including SSDs, can be infected. Kaspersky does note that the firmware reprogramming appears to be extremely rare, they've only identified a few victim who were targeted by this kind of attack. The firm speculate the Equation Group reserves HDD reprogramming for the most valuable victims or for some very unusual circumstances.
The malware originates from the "Equation Group", an organisation believed to have ties with the US government, and Kaspersky claims the complexity and scale of the operation makes Stuxnet seem like child play. A 44-page long report that details Kaspersky's findings can be read over here (PDF). Reuters spoke to its sources and received confirmation that the NSA is behind these attacks.
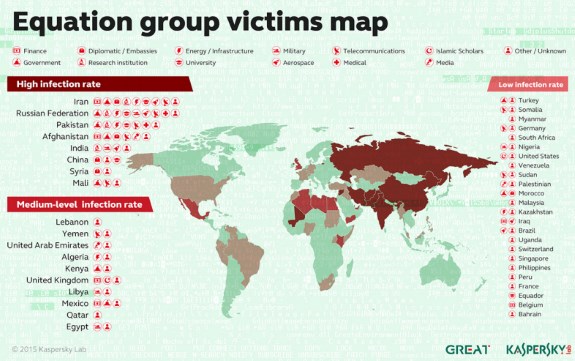
Victims of the Equation group were observed in more than 30 countries, including Iran , Russia , Syria , Afghanistan , Kazakhstan , Belgium , Somalia , Hong Kong , Libya , United Arab Emirates , Iraq , Nigeria , Ecuador , Mexico , Malaysia , United States , Sudan , Lebanon , Palestine , France , Germany , Singapore , Qatar , Pakistan , Yemen , Mali , Switzerland , Bangladesh , South Africa , Philippines , United Kingdom , India and Brazil .
Equation has been active perhaps as early as 1996, but it boosted its operations in 2008, developing several incredibly powerful cyberweapons, Kaspersky named these tools Equationdrug, Doublefantasy, Triplefantasy, Grayfish, Fanny and Equationlaser. Together, this malware suite was able to infect Windows computers, USB sticks and even hard drive firmware, letting Equation steal data from targeted computers and stay undetected for years.
...
All in all, Kaspersky counted more than 500 infections globally, many on important, server-type machines. However, infections have a self-destruct mechanism, meaning there may have been many more, which are now undetectable.
Source: Mashable