Posted on Tuesday, March 13 2018 @ 15:49 CET by Thomas De Maesschalck
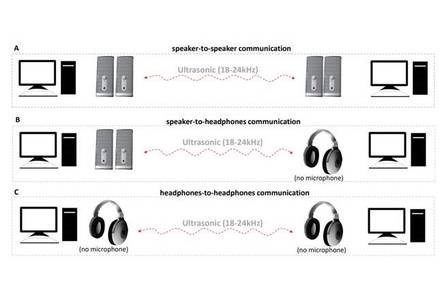
Cybersecurity researchers from Israel's Ben-Gurion University of the Negev published an academic paper that highlights how it's possible to steal data from airgapped PCs using speakers or headphones. It's not really a major secret, but it's possible to turn a speaker into a microphone. This basically enables inaudible ultrasonic sound wave transmissions between two speakers or headphones. This feature is possibly via "jack retasking", a feature enabled by various audio chipsets.
Full details
The Register.
MOSQUITO, the researchers explain, demonstrates that speakers can covertly transmit data between unconnected machines at a distance of up to nine meters. What's more, the technique works between mic-less headphones – the researchers say their work is the first to explore headphone-to-headphone covert communication.
Speakers, the paper explains, can be thought of as microphones working in reverse: Speakers turn electrical signals into acoustic signals while microphones turn acoustic signals into electrical ones. And each includes a diaphragm to assist with the conversion, which can help reverse the process.
Modern audio chipsets, such as those from Realtek, include an option to alter the function of the audio port via software, the paper explains. This capability is referred to as "jack retasking."